NA:Blockchain Security
Blockchain Security vs. Standard Cybersecurity
Blockchain is commonly called the future of computing. It takes a very different approach to data storage and processing and requires a very different perspective for security.
In this section, we will discuss some of the ways that security differs in traditional and blockchain environments.
=======================================================
Video: Introduction to Blockchain Security vs. Standard Cybersecurity
Blockchain Security vs. Standard Cybersecurity: The Environment
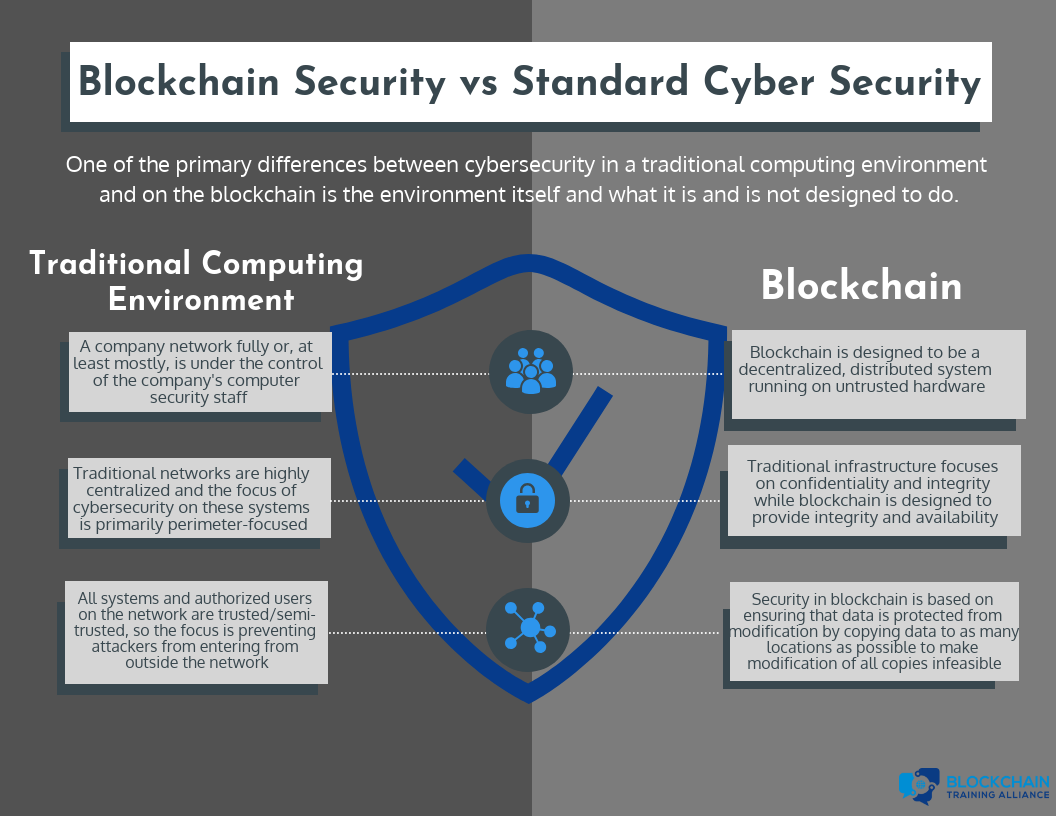
One of the primary differences between cybersecurity in a traditional computing environment and on the blockchain is the environment itself and what it is and isn't designed to do.
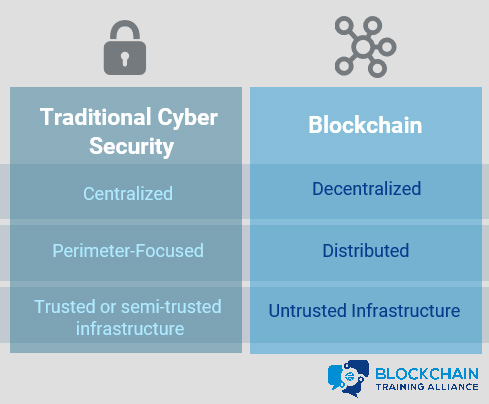
The traditional computing environment is a company network fully or, at least mostly, under the control of the company's computer security staff. While many organizations are making the shift to cloud-based environments, they still have a high degree of control over the security and configuration of their rented systems. Traditional networks are highly centralized, and the focus of cybersecurity on these systems is primarily perimeter-focused. All systems and authorized users on the network are trusted or semi-trusted, so the focus is on preventing attackers from entering from outside the network.
Blockchain is designed to be a decentralized, distributed system running on untrusted hardware. While security in traditional environments is designed to provide security by putting all data in one place and building walls around it, security in blockchain is based on ensuring that data is protected from modification by copying data to as many locations as possible to make modification of all copies infeasible. Traditional infrastructure focuses on confidentiality and integrity, while blockchain is designed to provide integrity and availability.
Blockchain Security vs. Standard Cybersecurity: Security
Both traditional computing environments and blockchain have security considerations associated with them. In many cases, the same attack is possible against both paradigms, but the details of how to implement it vary.
Here, we discuss how a few different attacks can be launched against traditional computing environments and blockchain:
- Denial-of-service
- Endpoint security
- Intentional misuse
- Code vulnerabilities
- Data protection.
Blockchain Security vs. Standard Cybersecurity: Denial-of-Service (DoS)
A denial-of-service (DoS) attack is when an attacker makes it impossible for a system to serve its users as designed. This can be accomplished by exploiting a flaw in the system, but, more commonly, is accomplished by performing legitimate actions at a rate higher than the target can handle.
To be effective, denial-of-service attacks typically focus on a system’s weakest link or bottleneck. In traditional environments, denial-of-service attacks target a company's web server to prevent customers from accessing the company's services. This can be accomplished by making more connection requests than the server is capable of supporting. In blockchain, a denial-of-service attack involves submitting more transactions to the blockchain than it can handle.
Since many blockchains have fixed-size blocks created at a fixed rate and are stored in a distributed fashion, they have a maximum capacity that a determined attacker can exceed, rendering the blockchain unusable.
======================================================
Blockchain Security vs. Standard Cybersecurity: Endpoint

Traditional infrastructure and blockchain environments also differ with regard to endpoint security. In traditional cyber, endpoints are under the control of the enterprise and have some level of heterogeneity. In blockchain, endpoints are the nodes and may be completely homogeneous.
Heterogeneity can be dangerous because an attacker has more options for finding a vulnerability to exploit, while homogeneity means that a flaw in one system is a flaw in all of the systems.
======================================================
Blockchain Security vs. Standard Cybersecurity: Code Vulnerabilities
Another way that traditional cybersecurity and blockchain differ is in the level of trust in the code used in a company's applications. In traditional cyber, the company writes most of the code, and vulnerabilities can arise only from code that the company controls.
In blockchain, anyone can write a smart contract, and a flaw in the smart contract or the underlying platform code can have wide-reaching consequences. The only hack to date against the Bitcoin network was enabled by an integer overflow vulnerability in the Bitcoin protocol.
When exploited, an attacker was able to assign himself more Bitcoin than was ever intended to be created. If the Bitcoin network didn't “break the rules” by modifying the historical ledger through a hard fork, Bitcoin would have become worthless. Anyone who wants to use Bitcoin has to accept the risks of hacks like this; they can't modify the code before including it in their application.
======================================================
Blockchain Security vs. Standard Cybersecurity: Intentional Misuse
Both traditional and blockchain environments are vulnerable to attacks based on intentional misuse of the system. In traditional cyber, insider attacks or intentional misuse of the system by clients are possible. In fact, a denial-of-service attack is a specific type of intentional misuse.
In blockchain, systems using Proof of Work incentivize miners to do something a lot, but not too much. The main weakness of Proof of Work is that a blockchain becomes insecure if more than half of the mining network's processing power is controlled by a single group.
Proof of Work incentivizes miners to control as much processing power as possible to win rewards, but doesn't want them to become too successful.
=======================================================
Blockchain Security vs. Standard Cybersecurity: Data Protection
Finally, traditional infrastructure and blockchain differ in their goals regarding data protection. In traditional cyber, data is siloed, and access is strictly controlled by the owners, placing responsibility for confidentiality, integrity, and availability in their hands.
In blockchain, data is distributed, and the blockchain is relied upon to provide integrity and availability.
=======================================================
Security: Public vs. Private Blockchains
Let's discuss the differences between a public and a private blockchain:
As the blockchain continues to evolve, the terminology has become confusing. Both public and private blockchains share many similarities:
- Both are decentralized peer-to-peer networks, each maintaining a shared append-only ledger of digitally-signed transactions.
- Both maintain transaction replicas in-sync through a protocol referred to as consensus.
- Both provide certain guarantees on the immutability of the ledger.
More importantly, the main difference between a public and private blockchain is related to who is allowed to participate in the network, execute the consensus protocol, and maintain the shared ledger.
A public blockchain network is completely open and anyone can join and participate in the network.
A private blockchain network requires an invitation, and must be validated by either the network starter or by a set of rules. Private blockchains are usually set up as permissioned networks, placing restrictions on who is allowed to participate in the network, and only in certain transactions.